
Table of Contents
What is Kubernetes Downward API
Kubernetes Downward API allows you to pass metadata about the pod and its environment through the use of environment variables or files. The Downward API is not a real API like Kubernetes API but is a way of getting pod metadata or status injected as environment variables or files.
What kind of metadata is available for injection?
By using Downward API you can expose the pod’s metadata to the container processes running inside the pod. The following metadata can be passed using Downward API:
- Name of the pod and its IP address
- The pod namespace and the node name where the pod is scheduled
- The service account name under which the pod is running
- The CPU and memory limits for each container in the pod
- The CPU and memory requests for each container in the pod
- The pod’s labels and annotations
The full list is available here on the Kubernetes.io website.
Pass Kubernetes Downward API metadata as environment variables
To pass Kubernetes Downward API metadata as environment variables, you can define the metadata fields in the pod’s env section and use the fieldRef property to reference the specific field from the Downward API.
Here’s an example of a pod specification YAML that demonstrates passing Downward API metadata as environment variables:
apiVersion: v1
kind: Pod
metadata:
name: downward-api-usage
spec:
containers:
- name: downward-api-container
image: busybox:latest
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: POD_IP
valueFrom:
fieldRef:
fieldPath: status.podIP
command: ["sh", "-c", "echo $POD_NAME $POD_NAMESPACE $POD_IP"]pod-envvariables.yaml
In this example, the env section defines three environment variables: POD_NAME, POD_NAMESPACE, and POD_IP. Each valueFrom property references a specific field from the Downward API using fieldRef and fieldPath.
When this pod is created, the container will have access to the values of metadata.name, metadata.namespace, and status.podIP as environment variables. In this case, the container’s entrypoint command echoes the values of these variables.
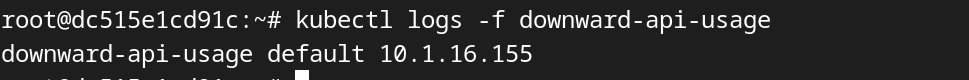
Pass Kubernetes Downward API metadata as environment volume
Here’s an example of a pod specification YAML that demonstrates passing Kubernetes Downward API metadata using a volume:
apiVersion: v1
kind: Pod
metadata:
name: downward-api-usage
spec:
containers:
- name: downward-api-container
image: busybox:latest
volumeMounts:
- name: metadata-volume
mountPath: /metadata
volumes:
- name: metadata-volume
downwardAPI:
items:
- path: pod_name
fieldRef:
fieldPath: metadata.name
- path: pod_namespace
fieldRef:
fieldPath: metadata.namespacepod-volume.yaml
In this example, a volume called metadata-volume is defined with downwardAPI as the volume source. The downwardAPI section specifies the fields from the Downward API and their corresponding paths. These fields are written to files inside the container at the specified paths (/metadata/pod_name and, /metadata/pod_namespace.
The container definition includes a volume mount metadata-volume that mounts the Downward API volume at the desired location (/metadata). Inside the container, you can read the values from the mounted files as environment variables.
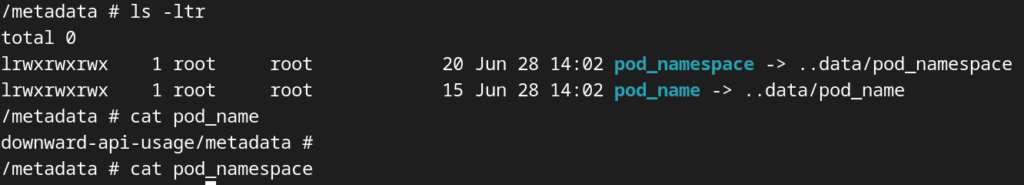
When to use Kubernetes Downward API
The Downward API in Kubernetes is useful in various scenarios where you need to expose pod metadata and other information to your running containers. Here are a few common use cases for the Downward API:
| Passing pod -specific metadata information | Pod metadata information, such as the pod name, namespace, IP address, labels, annotations, and more, can be passed as environment variables within your pod containers. |
| Passing pod-specific metadata information | You can expose container-specific metadata, such as the container name, container ID, resource limits, resource requests, and container termination reason, as environment variables. |
| Injecting configuration parameters | You can utilize the Downward API to inject configuration parameters into your containers at runtime. For example, you can expose values from ConfigMaps or Secrets as environment variables using the Downward API. This provides a way to dynamically configure your application without requiring modifications to your container image or manifest files. |
| Enabling dynamic scaling and self-awareness | The Downward API can be leveraged to enable self-awareness and dynamic scaling of your applications. By exposing metrics, such as CPU and memory usage, as environment variables, you can build logic within your application to scale horizontally or adjust its behavior based on the available resources or load conditions. |
| Integrating with external systems | When your containers need to interact with external systems or services, you can pass credentials, URLs, or other connection information through the Downward API as environment variables. This allows your containers to retrieve the necessary information without hardcoding it, increasing flexibility and security. |
Conclusion
Kubernetes Downward API is valuable when you require pod-level or container-level metadata to be accessible within your containers. It provides a convenient mechanism for passing information as environment variables or files, enabling better configuration management, dynamic behavior, and integration with the Kubernetes environment and external systems.
FAQ’s
Can Downward API be used to retrieve information about other pods or nodes?
No, the Downward API is limited to providing information about the current pod and its environment. It does not support retrieving information about other pods or nodes in the cluster.
Can I use the Downward API in both pods and init containers?
Yes, the Downward API can be used in both regular containers and init containers within a pod. It allows you to access pod-specific information from any container running in the pod.
Are there any security considerations when using the Downward API?
Yes, be cautious about exposing sensitive information through environment variables or volume files. Ensure that any sensitive data is properly secured and accessed only by authorized containers within the same pod.
Please explore our other articles on Kubernetes.
