
Table of Contents
What is an Image Vulnerability Scanner?
Image Vulnerability scanners are tools used to identify and assess any security vulnerabilities in container images. These scanners can help to scan and analyze container images for known security weaknesses, misconfigurations, or outdated software versions that could potentially be exploited by attackers. These scanners typically analyze the container image and compare it against a database of known vulnerabilities. The scanners provide information on the severity of the vulnerabilities found, along with recommendations for their remediation. The end goal of the scanning exercise is to identify potential weaknesses that could be exploited by attackers to gain unauthorized access, cause system disruptions, or steal sensitive information. These tools provide detailed reports on discovered vulnerabilities, along with recommendations for remediation or mitigation.
Here is a list of popular Image Vulnerability Scanners that you can use to find any security weaknesses, misconfigurations, or outdated software versions in your container images.
Trivy
Trivy is a popular open-source vulnerability scanner that can be used to scan container images for vulnerabilities. It is a fast and accurate scanner that can scan images for a wide range of vulnerabilities, including:
- Common vulnerabilities and exposures (CVEs)
- Security advisories
- Software bill of materials (SBOMs)
Installation
Trivy can be easily installed on various operating systems. The complete installation instructions are available on the Trivy website.
RedHat/Centos Installation:
rpm -ivh https://github.com/aquasecurity/trivy/releases/download/v0.43.0/trivy_0.43.0_Linux-64bit.rpmUbuntu Installation:
wget https://github.com/aquasecurity/trivy/releases/download/v0.43.0/trivy_0.43.0_Linux-64bit.deb
sudo dpkg -i trivy_0.43.0_Linux-64bit.debHomebrew for macOS Installation:
brew install trivyUsage
You can simply specify your image name and Trivy scans and detects known vulnerabilities in your container image.
trivy <target> [--scanners <scanner1,scanner2>] <subject>To enable only vulnerability scanning, you can specify --scanners vuln.
trivy image --scanners vuln [YOUR_IMAGE_NAME]To check for Licenses:
trivy image --scanners license [YOUR_IMAGE_NAME]Various options are documented here on Trivy website.
Example: To scan RedHat UBI8 image for both secrets and vulnerabilities you will issue the below command:
trivy image registry.access.redhat.com/ubi8/ubi-minimal:8.6-751Scan Result:
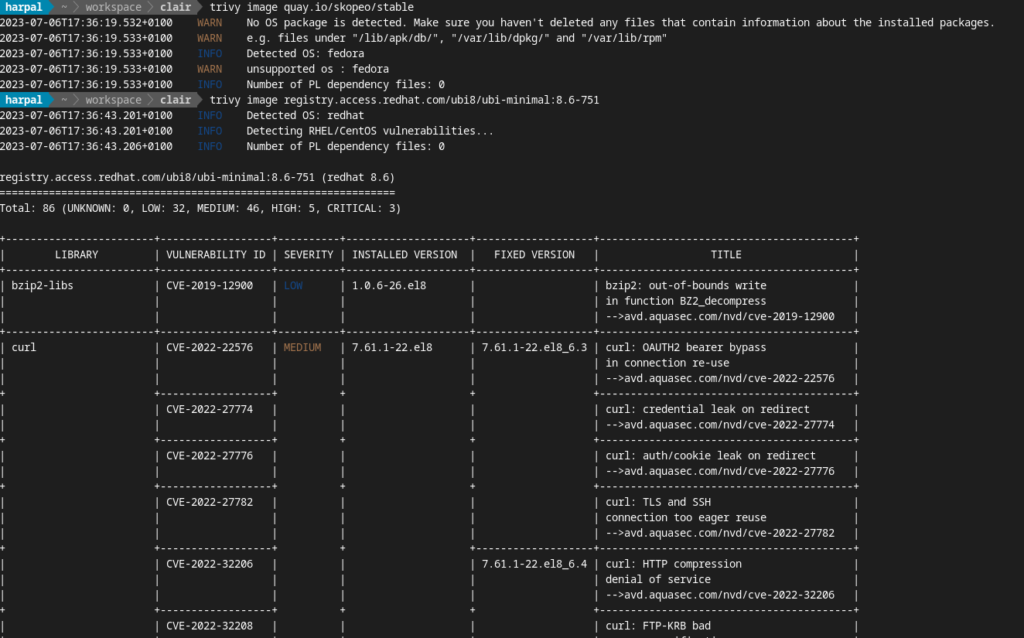
Benefits
Some of the benefits of using Trivy:
- It is fast and accurate. Trivy can scan images quickly and accurately. This makes it a good choice for scanning large images or images that are updated frequently.
- It is easy to use. Trivy is a command-line tool that is easy to use. You can scan images locally or remotely using the Trivy command-line interface.
- It is free and open-source. Trivy is a free and open-source tool. This means that anyone can use it, and the source code is available for anyone to inspect.
Limitations
Some limitations of using Trivy:
- It can be slow to scan large images. Trivy can be slow to scan large images. This is because Trivy needs to scan the entire image to identify vulnerabilities.
- It does not scan for all vulnerabilities. Trivy does not scan for all vulnerabilities. It only scans for vulnerabilities that are known to Trivy.
- It is not as comprehensive as some other vulnerability scanning tools. There are other vulnerability scanning tools that are more comprehensive than Trivy. These tools can scan for a wider range of vulnerabilities.
Snyk CLI
Snyk Cli is a vulnerability scanner that can be used to scan container images, code, and open-source dependencies for vulnerabilities. It is a cloud-based service that can be used by anyone to scan their applications for security risks.
Snyk has a number of features that make it a valuable tool for security teams, including:
- Scans for a wide range of vulnerabilities: Snyk scans for a wide range of vulnerabilities, including CVEs, security advisories, and license violations.
- Scans container images, code, and open source dependencies: Snyk can scan container images, code, and open source dependencies for vulnerabilities. This makes it a valuable tool for teams that use a variety of technologies.
- Provides actionable insights: Snyk provides actionable insights that can be used to fix vulnerabilities. This includes information about the vulnerability, the affected components, and how to fix the vulnerability.
- Easy to use: Snyk is easy to use and can be integrated with a variety of CI/CD tools. This makes it a valuable tool for teams that want to automate their vulnerability scanning process.
Installation
The complete installation instructions are available on the Snyk site.
MacOs Installation:
curl --compressed https://static.snyk.io/cli/latest/snyk-macos -o snyk
chmod +x ./snyk
mv ./snyk /usr/local/bin/Homebrew Installation:
brew tap snyk/tap
brew install snykUsage
snyk auth [<API_TOKEN>] [<OPTIONS>]The snyk auth command authenticates your machine to associate the Snyk CLI with your Snyk account. You can register for a free account on the Snyk portal. After you have authenticated, you can start using the CLI.
To scan the container image you can issue the below command:
snyk container test <YOUR_IMAGE_NAME>Benefits
Some of the benefits of using Snyk are:
- It is easy to use. Snyk has a user-friendly interface that makes it easy to scan your applications for vulnerabilities.
- It is comprehensive. Snyk can scan a wide range of vulnerabilities, including CVEs, security advisories, and license violations.
- It is accurate. Snyk has a high accuracy rate, so you can be confident that the vulnerabilities that it finds are real.
- It is integrated with CI/CD tools. Snyk can be integrated with a variety of CI/CD tools, so you can automate your vulnerability scanning process.
Limitations
Some of the limitations of using Snyk are:
- It can be expensive. Snyk is a paid service, so you will need to pay for a subscription.
- It can be slow to scan large applications. Snyk needs to scan the entire application to identify vulnerabilities, so it can be slow to scan large applications.
- It does not scan for all vulnerabilities. Snyk does not scan for all vulnerabilities. It only scans for vulnerabilities that are known to Snyk.
Grype
Grype is a vulnerability scanner developed by Aqua Security that can be used to scan container images for vulnerabilities and other security issues. Grype is a command-line tool that can be used to scan images locally or remotely for a variety of vulnerabilities, including:
- Common vulnerabilities and exposures (CVEs)
- Security advisories
- Software bill of materials (SBOMs)
Grype also includes a number of features that make it a powerful tool for scanning container images, including:
- The ability to scan images for vulnerabilities in their dependencies
- The ability to scan images for vulnerabilities that have been patched in newer versions of the image
- The ability to scan images for vulnerabilities that have been reported but not yet patched
Installation
Currently, Grype is built only for macOS and Linux.
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b /usr/local/binHomebrew Installation:
brew tap anchore/grype
brew install grypeUsage
To scan for vulnerabilities in an image:
grype <image>The above command scans for vulnerabilities that are visible in the container (i.e., the squashed representation of the image). To include software from all image layers in the vulnerability scan, regardless of its presence in the final image, provide --scope all-layers:
grype <image> --scope all-layersTo run grype from a Docker container so it can scan a running container, use the following command:
docker run --rm \
--volume /var/run/docker.sock:/var/run/docker.sock \
--name Grype anchore/grype:latest \
$(ImageName):$(ImageTag)You can have Grype exit with an error if any vulnerabilities are reported at or above the specified severity level. This comes in handy when using Grype within a script or CI pipeline. To do this, use the --fail-on <severity> CLI flag.
For example, here’s how you could trigger a CI pipeline failure if any vulnerabilities are found in the ubuntu:latest image with a severity of “medium” or higher:
grype ubuntu:latest --fail-on mediumBenefits
Here are some of the benefits of using Grype:
- It can scan images for a variety of vulnerabilities. Grype can scan images for a variety of vulnerabilities, including CVEs, security advisories, and SBOMs. This makes it a powerful tool for identifying and mitigating security risks in container images.
- It can scan images for vulnerabilities in their dependencies. Grype can scan images for vulnerabilities in their dependencies. This is important because vulnerabilities in dependencies can be just as dangerous as vulnerabilities in the image itself.
- It is easy to use. Grype is a command-line tool that is easy to use. You can scan images locally or remotely using the Grype command-line interface.
- It is free and open-source. Grype is a free and open-source tool. This means that anyone can use it, and the source code is available for anyone to inspect.
Limitations
Here are some of the limitations of Grype:
- It can be slow to scan large images. Grype can be slow to scan large images. This is because Grype needs to scan the entire image to identify vulnerabilities.
- It does not scan for all vulnerabilities. Grype does not scan for all vulnerabilities. It only scans for vulnerabilities that are known to Grype.
- It is not as comprehensive as some other vulnerability scanning tools. There are other vulnerability scanning tools that are more comprehensive than Grype. These tools can scan for a wider range of vulnerabilities.
Clair v4
Clair is an application for parsing image contents and reporting vulnerabilities affecting the contents. This is done via static analysis and not at runtime.
Clair supports the extraction of contents and assignment of vulnerabilities from the following official base containers:
- Ubuntu
- Debian
- RHEL
- Suse
- Oracle
- Alpine
- AWS Linux
- VMWare Photon
- Python
Clair v4 utilizes the ClairCore library as its engine for examining contents and reporting vulnerabilities.
Installation
Clair is officially packaged and released as a container at quay.io/projectquay/clair.
Usage
Here are the steps on how to scan an image using Clair v4:
- Install the Clair microservices. You can find the installation instructions on the Clair website.
- Configure Clair to scan your images. You will need to provide Clair with the location of your images and the vulnerability database that you want to use.
- Scan your images. You can scan your images using the Clair API or the Clair web UI.
- View scan results. You can view scan results in the Clair web UI or by using the Clair API.
Here are the commands to scan an image using the Clair API:
curl -X POST \
-H "Content-Type: application/json" \
-d '{
"image": "my-image:latest"
}' \
http://localhost:6060/v1/images/scanThe response will be a JSON object that contains the scan results.
You can also use Clair Web UI to submit an image scan.
Benefits
Here are some of the benefits of using Clair:
- Improved accuracy: Clair v4 uses a new machine-learning model that is more accurate at identifying security vulnerabilities in containers.
- Reduced false positives: Clair v4 has a number of new features that help to reduce the number of false positives, making it easier to focus on genuine security threats.
- Increased scalability: Clair v4 is more scalable than previous versions, making it easier to use for large container deployments.
- Improved usability: Clair v4 has a number of new features that make it easier to use, such as a new web UI and a command-line tool.
Limitations
Here are some of the limitations of Clair:
- Dependency on external sources: Clair v4 relies on external sources for vulnerability data, such as the Common Vulnerabilities and Exposures (CVE) database. This means that the accuracy of Clair v4’s vulnerability scans is dependent on the accuracy of the data in these external sources.
- Not all vulnerabilities are detected: Clair v4 is not able to detect all vulnerabilities in container images. This is because some vulnerabilities are not known or not yet added to the vulnerability databases that Clair v4 uses.
- Requires manual configuration: Clair v4 requires some manual configuration, such as the selection of vulnerability databases and the definition of scan policies. This can be a time-consuming process, especially for large container deployments.
- Can be resource-intensive: Clair v4 can be resource-intensive, especially for large container deployments. This is because it needs to scan the images and compare them to the vulnerability databases.
- Not always up-to-date: The vulnerability databases that Clair v4 uses are not always up-to-date. This means that Clair v4 may not be able to detect the latest vulnerabilities.
- Not suitable for all environments: Clair v4 is not suitable for all environments. For example, it is not suitable for environments where there is a high volume of container images being scanned.
Conclusion
Vulnerability scanners should be used in conjunction with other security practices such as regular patch management, secure coding practices, access controls, and ongoing monitoring to establish a robust security posture.
Please read our other articles on container concepts and security.
